DNSSEC enabled for domain names on our platform
 The easy-to-remember domain names that we all use are translated into numerical IP addresses, which are needed for network identification and location by the hierarchical Domain Name System (DNS).
The easy-to-remember domain names that we all use are translated into numerical IP addresses, which are needed for network identification and location by the hierarchical Domain Name System (DNS).
This way, client-server communication can be performed and it lies at the basis of the web.
However, like every other system, DNS is not invulnerable. Since its introduction in 1983 and especially after the mass popularization of the Internet that started in the late 90s, hackers and hijackers have made countless attempts to compromise it.
They often try to sneak into users’ sessions and collect various private details. Then they use those for the registration of fake websites, user profiles in various places and/or withdrawing money from bank accounts.
The DNSSEC technology was developed in order to restrict all of the aforementioned malicious activities, including the growingly popular domain hijacking.
Today, we are glad to welcome this cutting-edge security technology on our cloud hosting platform.
Why was DNSSEC created?
An old vulnerability of the DNS lookup process re-emerged just a couple of years ago.
Although it seemed to have been long forgotten by everyone, it was recently re-discovered that the Domain Name System is unable to verify neither the validity nor the integrity of the data which is exchanged after a DNS query has been sent. The reason for this is trivial – the DNS was not designed to check for credentials whenever a DNS lookup is performed.
Therefore, domain hijackers can sneak through during a DNS lookup. Then, they could use the session for malicious activities like phishing.
In other words, a new layer of protection was needed as quickly as possible. In response, the DNSSEC security protocol was introduced.
How does DNSSEC work?
The DNSSEC makes the DNS lookup more secure by making sure that a user always connects to the verified website or service corresponding to a domain name.
It adds digital signatures to each and every step of the query process. These signatures are then validated, so when you type in a web address inside the address bar of your browser, you can rest assured that you’ll get to the genuine website even if fake ones have been created by hackers.
This is an illustration of what the DNSSEC security protocol does:
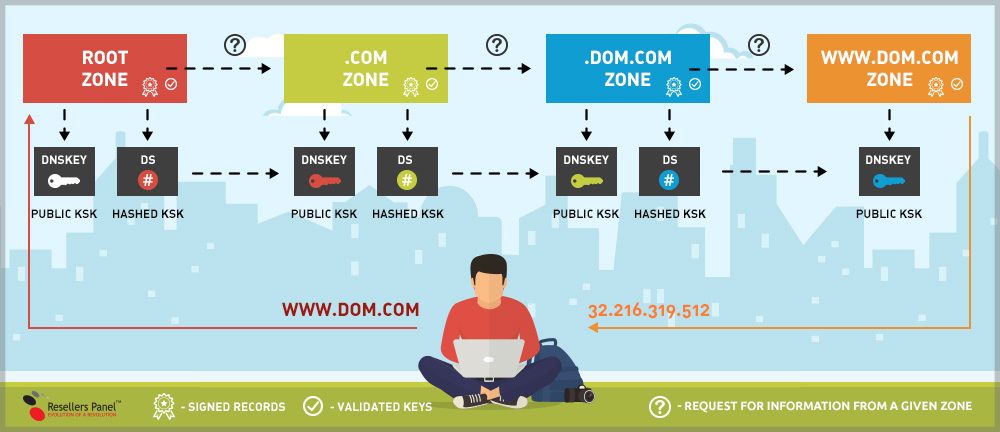
Each digital signature is generated by a special key. Then, the key has to be verified by a higher-level entity. To give you an example: .COM is in charge of signing .DOM.COM’s key and the root is responsible for signing .COM’s key.
A parent zone is responsible for signing the child zone which is positioned underneath. This way, the so-called ‘chain of trust’ is formed between the zones.
All of the afore-mentioned digital signatures along with their keys can be found on the name servers. Common record types like: A, AAAA, MX and CNAME are stored there as well.
Then the requested DNS record’s signature is checked for verification of its corresponding name server. As a result, it’s easy to tell whether a given digital signature comes unaltered from its corresponding name server or a man-in-the-middle attack has occurred at some point.
Which TLDs support DNSSEC?
Since we are an ICANN-accredited domain name registrar, we can offer full DNSSEC support for the following TLDs: .COM, .NET and the .BIZ.
We are officially allowed to publish the DS records corresponding to each domain name which is registered with the aforementioned generic extensions.
We are also in the process of adding more and more TLDs to that list. Keep an eye on our blog for more news on the subject.
***
DNSSEC can be vital for the reputation of a domain name. If domain security is neglected, website visitors can become subject to frauds – loss of personal information or even identity theft. And customers will not return to a site that they deem to be insecure or harmful.
This is why you can use the native DNSSEC support as a great marketing tool when your advertise your hosting services.

Leave a Reply